
The latest sy0-601 dumps are the best material for the CompTIA Security+ certification exam! 1093 latest exam questions and answers that fully cover the CompTIA Security+ topic exam and are reviewed by a team of CompTIA certification experts the correction has been verified in real scenarios, and it is real and effective! Candidates can use the Latest sy0-601 dumps with PDF and VCE: https://www.leads4pass.com/sy0-601.html to help you practice easily and guarantee 100% success in passing the exam.
Important! Share some of the latest sy0-601 dumps exam questions online practice for free
| From | Number of exam questions | Associated certification | Online Download |
| Pass4itsure | 15 | CompTIA Security+ | SY0-601 PDF |
QUESTION 1:
After gaining access to a dual-homed (i.e.. wired and wireless) multifunction device by exploiting a vulnerability in the device\’s firmware, a penetration tester then gains shell access on another networked asset This technique is an example of:
A. privilege escalation
B. footprinting
C. persistence
D. pivoting.
Correct Answer: D
Pivoting -> The act of an attacker moving from one compromised system to one or more other systems on the network
QUESTION 2:
After entering a username and password, an administrator must draw a gesture on a touch screen. Which of the following demonstrates what the administrator is providing?
A. Multifactor authentication
B. Something you can do
C. Biometric
D. Two-factor authentication
Correct Answer: B
QUESTION 3:
A global pandemic is forcing a private organization to close some business units and reduce staffing at others.
Which of the following would be BEST to help the organization\’s executives determine the next course of action?
A. An incident response plan
B. A communications plan
C. A disaster recovery plan
D. A business continuity plan
Correct Answer: D
QUESTION 4:
Ann, a customer, received a notification from her mortgage company stating her PII may be shared with partners, affiliates, and associates to maintain day-to-day business operations. Which of the following documents did Ann receive?
A. An annual privacy notice
B. A non-disclosure agreement
C. A privileged-user agreement
D. A memorandum of understanding
Correct Answer: A
From CompTIA’s official textbook:
“A privacy notice is typically an externally-facing document informing customers, users, or stakeholders about what the organization does with PII. It\’s also called a privacy statement.”
QUESTION 5:
After a recent security incident, a security analyst discovered that unnecessary ports were open on a firewall policy for a web server. Which of the following firewall policies would be MOST secure for a web server?
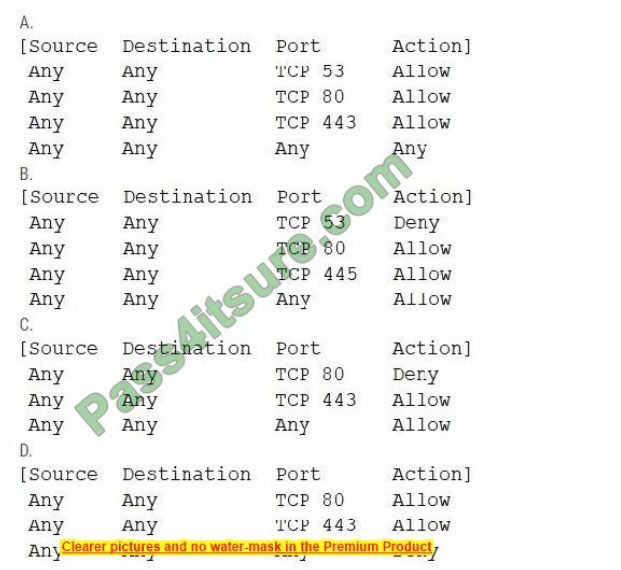
A. Option A
B. Option B
C. Option C
D. Option D
Correct Answer: D
QUESTION 6:
As part of a security compliance assessment, an auditor performs automated vulnerability scans. In addition, which of the following should the auditor do to complete the assessment?
A. User behavior analysis
B. Packet captures
C. Configuration reviews
D. Log analysis
Correct Answer: D
A vulnerability scanner is essentially doing that. It scans every part of your network configuration that it can and determines if known vulnerabilities are known at any point of that.
QUESTION 7:
A security analyst is configuring a large number of new company-issued laptops. The analyst received the following requirements:
1.
The devices will be used internationally by staff who travel extensively.
2.
Occasional personal use is acceptable due to the travel requirements.
3.
Users must be able to install and configure sanctioned programs and productivity suites.
4.
The devices must be encrypted
5.
The devices must be capable of operating in low-bandwidth environments.
Which of the following would provide the GREATEST benefit to the security posture of the devices?
A. Configuring an always-on VPN
B. Implementing application whitelisting
C. Requiring web traffic to pass through the on-premises content filter
D. Setting the antivirus DAT update schedule to weekly
Correct Answer: A
1-hackers spying on network traffic
2-they can still install stuff. app listing would only allow stuff IT OK\’d. Do you want to tell IT all your personal apps?
3-Sure can
4-network traffic is encrypted. These better have minimum TPM and antimalware on them.
5-Always on VPN is faster than a regular VPN – our company has been using it for years.
QUESTION 8:
A company recently experienced an attack during which the #5 main website was directed to the attacker \’s web server, allowing the attacker to harvest credentials from unsuspecting customers.
Which of the following should the company Implement to prevent this type of attack from occurring in the future?
A. IPSec
B. SSL/TLS
C. DNSSEC
D. S/MIME
Correct Answer: B
QUESTION 9:
In a phishing attack, the perpetrator is pretending to be someone in a position of power in an effort to influence the target to click or follow the desired response. Which of the following principles is being used?
A. Authority
B. Intimidation
C. Consensus
D. Scarcity
Correct Answer: B
Whaling is highly tailored to their audiences and often includes the victim\’s name, job title, and basic details that make the communications look legitimate.
QUESTION 10:
A network administrator needs to build out a new data center, with a focus on resiliency and uptime. Which of the following would BEST meet this objective? (Choose two.)
A. Dual power supply
B. Off-site backups
C. Automatic OS upgrades
D. NIC teaming
E. Scheduled penetration testing
F. Network-attached storage
Correct Answer: AB
Dual PS keeps the servers up / a DRS will conform to the question of resiliency: Site Resiliency Resiliency of a site should include consideration of sites used to continue operations. Site resiliency considerations can be connected to the idea of restoration sites and their availability.
Related to the location of backup storage is where the restoration services will be located. If the organization has suffered physical damage to its facility, having offsite data storage is only part of
the solution.
This data will need to be processed somewhere, which means that computing facilities similar to those used in normal operations are required. These sites are referred to as recovery sites. The recovery problem can be approached in a number of ways, including hot sites, warm sites, and cold sites.
https://searchdatacenter.techtarget.com/definition/resiliency
QUESTION 11:
A RAT that was used to compromise an organization\’s banking credentials were found on a user\’s computer.
The RAT evaded antivirus detection. It was installed by a user who has local administrator rights to the system as part of a remote management toolset.
Which of the following recommendations would BEST prevent this from reoccurring?
A. Create a new acceptable use policy.
B. Segment the network into trusted and untrusted zones.
C. Enforce application whitelisting.
D. Implement DLP at the network boundary
Correct Answer: C
Having a list of allowed apps decreases the risk of an unwanted application with malware being installed.
QUESTION 12:
The following are the logs of a successful attack.
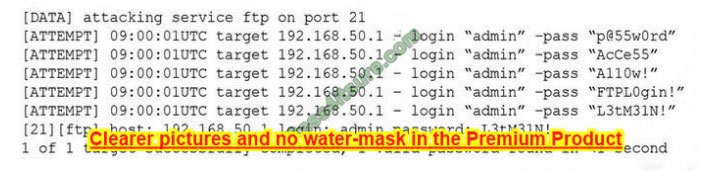
Which of the following controls would be BEST to use to prevent such a breach in the future?
A. Password history
B. Account expiration
C. Password complexity
D. Account lockout
Correct Answer: D
QUESTION 13:
A security analyst is investigating a vulnerability in which a default file permission was set incorrectly. The company uses non-credentialed scanning for vulnerability management.
Which of the following tools can the analyst use to verify the permissions?
A. ssh
B. chmod
C. ls
D. setuid
E. nessus
F. nc
Correct Answer: B
chmod is used to set permissions for the file.
If you use: ls -l
…
The latest sy0-601 dumps, fully updated in July, meet all the requirements to pass the CompTIA Security+ certification exam!
Candidates can verify the latest CompTIA Security+ certification topic exam questions through online practice to help them understand the latest exam scenarios! Download Latest sy0-601 dumps: https://www.leads4pass.com/sy0-601.html
, use PDF and VCE tools to practice 1093 latest CompTIA Security+ exam questions to help you pass the exam easily.