For complete and comprehensive CompTIA CySA+ exam preparation, you can try our just-updated CS0-002 exam dumps questions, and with it, you have the most reliable exam materials. This is helpful for successfully passing the CompTIA Cybersecurity Analyst (CySA+) exam.
Get excellent CS0-002 exam materials easily from the Pass4itSure CS0-002 exam dumps webpage https://www.pass4itsure.com/cs0-002.html. Practice valid CS0-002 exam questions and answers to successfully pass the exam.
[Free] Download CompTIA CS0-002 Dumps PDF 2022: https://drive.google.com/file/d/1usNOTsctqvwA3sbx8lIXw54SAdLML1mk/view?usp=share_link
Information about CompTIA’s CS0-002 exam:
- Exam Codes CS0-002
- Number of Questions Maximum of 85 questions
- Type of Questions Multiple choice and performance-based
- Length of Test 165 minutes
- Passing Score 750 (on a scale of 100-900)
- Price $392 USD
How do I prepare for the CompTIA CS0-002 exam?
First of all, you need reliable exam material. Here are the recommended Pass4itSure CS0-002 exam dumps.
Use the Pass4itSure CS0-002 exam dumps to use the practice questions inside as exam materials to prepare for the exam, and success is yours.
Pass4itSure materials for you to prepare:
- CS0-002 PDF
- CS0-002 VCE
All contain the latest exam practice questions and explanations to help you flexibly prepare for the CompTIA Cybersecurity Analyst (CySA+) exam.
Where can I get the latest dumps and Q/A for the CompTIA CS0-002?
Here you can, Softwarexam.com. I will share the website of the CS0–002 dumps – Pass4itSure. It is the most recent website related to CS0–002 dumps. This site is effective and can help you a lot.
You can read the latest CS0-002 exam questions 1-13 below (free of charge)
[2022.11] New CompTIA Cybersecurity Analyst (CySA+) Free CS0-002 Dumps Questions
NEW QUESTION 1
A cybersecurity analyst is investigating an incident report concerning a specific user workstation. The workstation is exhibiting high CPU and memory usage, even when first started, and network bandwidth usage is extremely high. The user reports that applications crash frequently, despite the fact that no significant changes in work habits have occurred.
An antivirus scan reports no known threats. Which of the following is the MOST likely reason for this?
A. Advanced persistent threat
B. Zero-day
C. Trojan
D. Logic bomb
Correct Answer: B
NEW QUESTION 2
In response to a potentially malicious email that was sent to the Chief Financial Officer (CFO), an analyst reviews the logs and identifies a questionable attachment using a hash comparison. The logs also indicate the attachment was already opened. Which of the following should the analyst do NEXT?
A. Create a sinkhole to block the originating server.
B. Utilize the EDR platform to isolate the CFO\\’s machine.
C. Perform malware analysis on the attachment.
D. Reimage the CFO\\’s laptop.
Correct Answer: A
Reference: https://bluecatnetworks.com/blog/dns-sinkhole-a-tool-to-help-thwart-cyberattacks/
NEW QUESTION 3
The Chief Executive Officer (CEO) instructed the new Chief Information Security Officer (CISO) to provide a list of enhancements to the company\\’s cybersecurity operation. As a result, the CISO has identified the need to align security operations with industry best practices. Which of the following industry references is appropriate to accomplish this?
A. OSSIM
B. NIST
C. PCI
D. OWASP
Correct Answer: B
Reference: https://www.nist.gov/sites/default/files/documents/itl/Cybersecurity_Green-Paper_FinalVersion.pdf
NEW QUESTION 4
A technician is running an intensive vulnerability scan to detect which ports are open to exploit. During the scan, several network services are disabled and production is affected. Which of the following sources would be used to evaluate? Which network service was interrupted?
A. Syslog
B. Network mapping
C. Firewall logs
D. NIDS
Correct Answer: A
NEW QUESTION 5
A team of security analysts has been alerted to potential malware activity. The initial examination indicates one of the affected workstations on beaconing on TCP port 80 to five IP addresses and attempting to spread across the network over port 445. Which of the following should be the team\\’s NEXT step during the detection phase of this response process?
A. Escalate the incident to management, who will then engage the network infrastructure team to keep them informed
B. Depending on the system critically remove each affected device from the network by disabling wired and wireless connections
C. Engage the engineering team to block SMB traffic internally and outbound HTTP traffic to the five IP addresses Identify potentially affected systems by creating a correlation
D. Identify potentially affected systems by creating a correlation search in the SIEM based on the network traffic.
Correct Answer: D
NEW QUESTION 6
An organization has the following risk mitigation policy:
1. Risks with a probability of 95% or greater will be addressed before all others regardless of the impact.
2. All other prioritization will be based on risk value. The organization has identified the following risks:
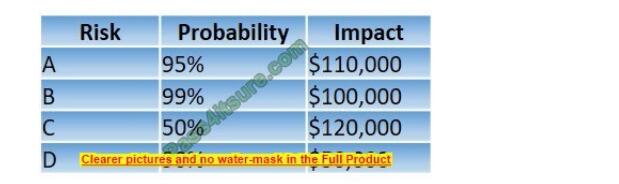
Which of the following is the order of priority for risk mitigation from highest to lowest?
A. A, B, D, C
B. A, B, C, D
C. D, A, B, C
D. D, A, C, B
Correct Answer: D
NEW QUESTION 7
A storage area network (SAN) was inadvertently powered off while power maintenance was being performed in a datacenter. None of the systems should have lost all power during the maintenance. Upon review, it is discovered that a SAN administrator moved a power plug when testing the SAN\\’s fault notification features.
Which of the following should be done to prevent this issue from reoccurring?
A. Ensure both power supplies on the SAN are serviced by separate circuits so that if one circuit goes down, the other remains powered.
B. Install additional batteries in the SAN power supplies with enough capacity to keep the system powered on during maintenance operations.
C. Ensure power configuration is covered in the data center change management policy and has the SAN administrator review this policy.
D. Install a third power supply in the SAN so the loss of any power intuit does not result in the SAN completely powering off.
Correct Answer: A
NEW QUESTION 8
A security analyst is investigating an incident that appears to have started with SOL injection against a publicly available web application. Which of the following is the FIRST step the analyst should take to prevent future attacks?
A. Modify the IDS rules to have a signature for SQL injection.
B. Take the server offline to prevent continued SQL injection attacks.
C. Create a WAF rule In block mode for SQL injection
D. Ask the developers to implement parameterized SQL queries.
Correct Answer: A
NEW QUESTION 9
An analyst finds that unpatched servers have undetected vulnerabilities because the vulnerability scanner does not have the latest set of signatures. Management directed the security team to have personnel update the scanners with the latest signatures at least 24 hours before conducting any scans, but the outcome is unchanged.
Which of the following is the BEST logical control to address the failure?
A. Configure a script to automatically update the scanning tool.
B. Manually validate that the existing update is being performed.
C. Test vulnerability remediation in a sandbox before deploying.
D. Configure vulnerability scans to run in credentialed mode.
Correct Answer: A
NEW QUESTION 10
An analyst was tasked with providing recommendations of technologies that are PKI X.509 compliant for a variety of secure functions. Which of the following technologies meets the compatibility requirement? (Select three.)
A. 3DES
B. AES
C. IDEA
D. PKCS
E. PGP
F. SSL/TLS
G. TEMPEST
Correct Answer: BDF
NEW QUESTION 11
Which of the following is MOST dangerous to the client environment during a vulnerability assessment penetration test?
A. There is a longer period of time to assess the environment.
B. The testing is outside the contractual scope
C. There is a shorter period of time to assess the environment
D. No status reports are included with the assessment.
Correct Answer: B
NEW QUESTION 12
A cybersecurity analyst is dissecting an intrusion down to specific techniques and wants to organize them in a logical manner. Which of the following frameworks would BEST apply in this situation?
A. Pyramid of Pain
B. MITRE ATTandCK
C. Diamond Model of Intrusion Analysis
D. CVSS v3.0
Correct Answer: B
NEW QUESTION 13
A security analyst is investigating a compromised Linux server. The analyst issues the ps command and receives the following output.
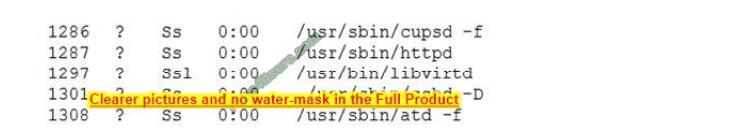
Which of the following commands should the administrator run NEXT to further analyze the compromised system?
A. strace /proc/1301
B. rpm -V openash-server
C. /bin/la -1 /proc/1301/exe
D. kill -9 1301
Correct Answer: A
Visit the Pass4itSure CS0-002 exam dumps website https://www.pass4itsure.com/cs0-002.html to get the latest exam materials and start your exam preparation journey.

